Protect Financial Accounts With These Class 12 Algebra Concepts
In recent years, India has seen a significant rise in the usage of Quick Responsive Code, popularly known as the QR code. This can be used for various experiences but is quite popular for monetary transactions with the help of payment platforms such as Paytm, PhonePe, BHIM, and on. This shift towards digital payment methods has been driven by the fact that technology in the form of smartphones and mobile internet is as easily available as air. The convenience and security offered by digital payment platforms have contributed to its popularity.

If there is free access, then there is also the fear of being hacked. This is one drawback of living in the digital world. Hence, the security of financial accounts is crucial for individuals and organisations alike. With cyber threats and attacks getting more sophisticated by the day, traditional methods of password protection and security measures are no longer hack-proof. As a result, there has been a growing need for stronger encryption methods to safeguard sensitive financial information.
One such method is the use of encrypted codes, which are based on advanced mathematical principles and algorithms. The implementation of encrypted codes requires a deep understanding of mathematics and Algebra, making it a topic of interest for students studying mathematics in higher education. So let's start with fundamental Algebra concepts discussed in Class 12 maths
Fundamental Concepts: Algebra Class 12
Class 12 Algebra covers a wide range of fundamental concepts that are essential for advanced mathematics and other fields of study. Some of the primary concepts taught in Class 12 Algebra include:
Matrices and determinants: Matrices are rectangular arrays of numbers, while determinants are used to find the properties of matrices, such as their inverses and solutions to systems of equations.
Relations and functions: Relations and functions are used to represent and analyse patterns and relationships between different sets of data.
Quadratic equations: Quadratic equations are used to solve problems involving quadratic functions, which have a parabolic shape and are commonly found in physics, engineering, and other fields.
Permutations and combinations: These concepts are used to calculate the number of possible arrangements or combinations of a set of objects or events.
Probability: Probability is used to determine the likelihood of an event occurring and is a crucial concept in statistics, finance, and other fields.
Binomial theorem: The binomial theorem is used to expand binomial expressions, which are expressions with two terms, such as (x + y)^2.
Limits and derivatives: Limits and derivatives are used to analyse the behaviour of functions as they approach certain values or points, and are essential for advanced calculus and other areas of mathematics.
These concepts form the basis for more advanced topics in mathematics, such Llinear Algebra, Differential Equations, and Calculus. Now come to encrypted codes. Do you know what these are?
What Is Encrypted Code?
An encrypted code is a set of characters or symbols that has been transformed into a different form using an encryption algorithm or method. QR codes and Barcodes are some examples of encrypted codes. The purpose of encryption is to protect sensitive information and make it unreadable to unauthorised parties who may try to access it without permission.
Encrypted Code: Type
Barcodes can be classified into two primary types: one-dimensional (1D) and two-dimensional (2D), which have distinct designs, features, and applications.
A 1D barcode comprises vertical stripes of varying width in black and white colours, along with a set of numbers below it. Such codes store information related to a product or service, such as item number, name, price, and other details. At supermarkets, cashiers typically scan 1D codes to retrieve product information at the point of sale.
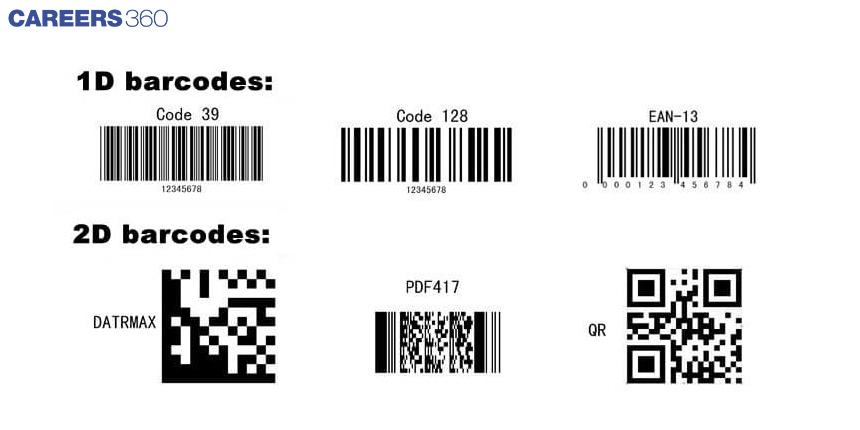
Two-dimensional codes (QR codes) are capable of storing a wide range of information such as text, website links, audio, video files, and illustrations. Scanning a QR code provides access to various platforms, including websites, landing pages, Facebook pages, TikTok accounts, and other sources that provide additional information regarding a product, service, special offer, or event. These codes can be found on several items such as business cards, postal packages, bus tickets, discount coupons, advertisement posters, and other types of media.
Also check - Metaverse, How Can It Impact Education And Learning
Mathematics Behind Encrypted Codes
Encryption is a technique that is used to secure data by transforming it into a format that is unreadable without a secret key or password. The process of encryption involves mathematical algorithms that are designed to convert plain text into a ciphertext that can only be decrypted by someone who has the correct key.
One of the most common encryption techniques used in modern cryptography is the RSA algorithm, which is based on the Class 12 Algebraic concept of prime factorization. The RSA algorithm works by selecting two large prime numbers, p, and q, and multiplying them together to generate a composite number, n. The values of p and q are kept secret, while n is made public.
Next, two additional numbers are generated: e and d. The number e is a small odd integer that is relatively prime to ( p - 1 ) * ( q - 1 ), while d is its inverse modulo ( p - 1 ) * ( q - 1 ). Modulo refers to a mathematical operation that calculates the remainder obtained when one integer is divided by another. The values of e and d are kept secret, while the values of n and e are made public.
To encrypt a message using the RSA algorithm, the sender first converts the message into a numerical form using a specific encoding method. Then, the sender raises the numerical value to the power of e modulo n, producing a ciphertext that can be sent to the receiver. Ciphertext is encrypted text transformed from plaintext using an encryption algorithm.
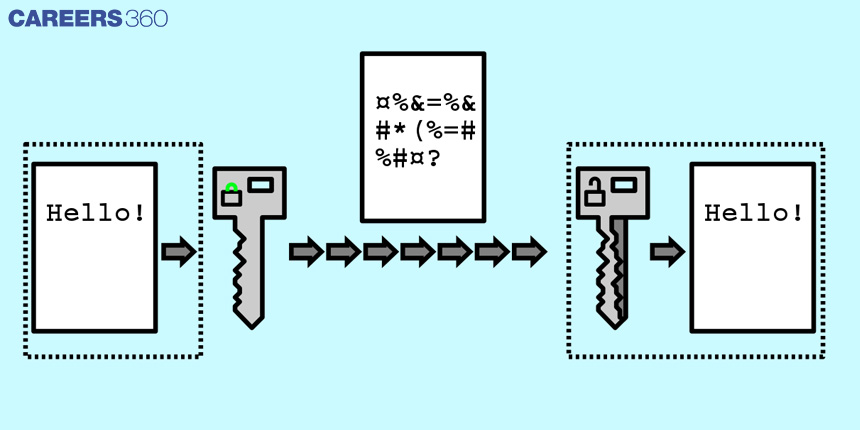
To decrypt the ciphertext, the receiver raises it to the power of d modulo n, which effectively reverses the encryption process and produces the original plaintext message.
Encryption algorithms rely on complex mathematical equations that are designed to make it difficult for unauthorised users to access sensitive data. By utilising these mathematical concepts, encrypted codes provide a secure means of transmitting information across a wide range of applications and industries.
Also check - Animal Vs Plant-Based Protein - What Is Your Best Source Of Protein?
Applications for Admissions are open.
As per latest syllabus. Physics formulas, equations, & laws of class 11 & 12th chapters
JEE Main Important Chemistry formulas
Get nowAs per latest syllabus. Chemistry formulas, equations, & laws of class 11 & 12th chapters
JEE Main high scoring chapters and topics
Get nowAs per latest 2024 syllabus. Study 40% syllabus and score upto 100% marks in JEE
JEE Main Important Mathematics Formulas
Get nowAs per latest syllabus. Maths formulas, equations, & theorems of class 11 & 12th chapters
