Blockchain: A New Approach To Secure Mathematical Data Transmission
In today's world, where technology is advancing rapidly, data security has become a major concern for individuals and organisations alike. With the increasing use of digital platforms for communication and transactions, there is a need for a secure and efficient method of data transmission that can ensure the privacy and integrity of information.

This is where Blockchain comes into the picture. It is a revolutionary technology that has the potential to transform the way we transmit and store data. At its core, Blockchain is a decentralised ledger that uses cryptography to ensure the security and immutability of data. Blockchain has gained immense popularity in recent years, particularly in the field of finance, where it is used for secure and transparent transactions. However, its potential applications go far beyond just finance including supply chain management, healthcare, and even voting systems.
So, how does Blockchain work and what makes it so secure? Well, the answer lies in its decentralised nature. Unlike traditional systems, where data is stored on a centralised server, Blockchain uses a network of computers to store and verify data. This makes it nearly impossible for hackers to tamper with the data or steal sensitive information.
In this article, we will delve deeper into the workings of Blockchain and explore its potential applications in various fields. We will also discuss the advantages and challenges of using Blockchain. So, sit back and get ready to explore the world of Blockchain!
Also Read | Solve The Travelling Salesman Problem With Graph Theory
What Is Blockchain?
Blockchain is basically a chain of blocks that contain data, with each block linked to the previous one through a unique code called a "hash." Once data is added to the Blockchain, it cannot be altered or deleted without altering the entire chain, making it immutable.
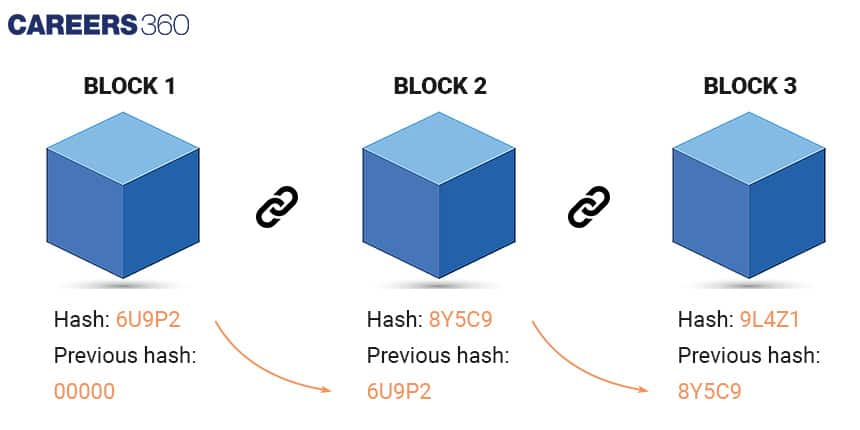
Blockchain-Related Technologies
Block Structure
The basic structure of a block in a Blockchain includes the following elements:
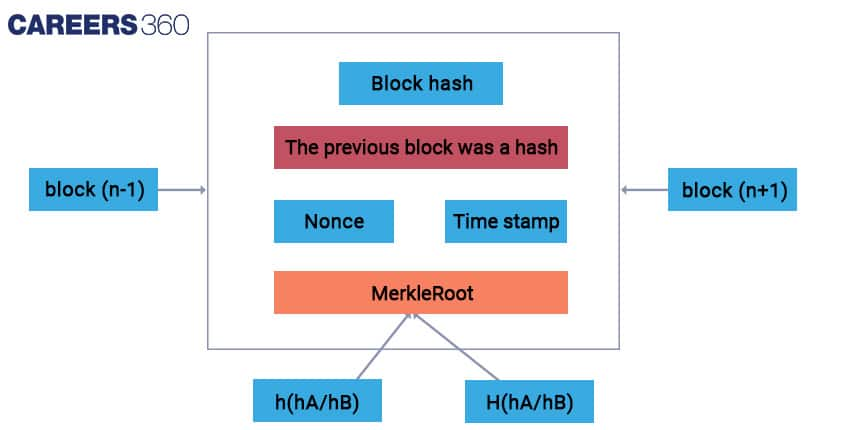
Block Header: The block header contains metadata about the block, including its version, timestamp, and the previous block's hash.
Merkle Tree: A Merkle tree is a data structure used to store all the transactions included in the block. It is constructed by recursively hashing pairs of transactions until a single root hash is obtained. The Merkle root hash is included in the block header and is used to verify that a transaction is included in the block.
Nonce: A nonce is a random number included in the block header that miners must find through a trial-and-error process.
Transactions: The transactions included in the block contain information about the sender, receiver, and amount transferred. Each transaction is cryptographically signed by the sender to ensure its authenticity.
When a block is created, it is broadcasted to the network, and all nodes on the network verify the transactions included in the block. If the transactions are valid, the block is added to the Blockchain, and the next block in the chain is created.
Also Read | Explore The Fascinating World of Black Holes: Formation, Properties, and Impact on the Universe
Consensus Algorithm
A consensus algorithm is a process used by Blockchain networks to verify transactions and maintain the integrity of the Blockchain. The goal of a consensus algorithm is to ensure that all nodes on the network agree on the current state of the Blockchain and that new transactions are added to the Blockchain in a secure and transparent manner.
There are several types of consensus algorithms, but two are the most common ones: PoW and PoS.
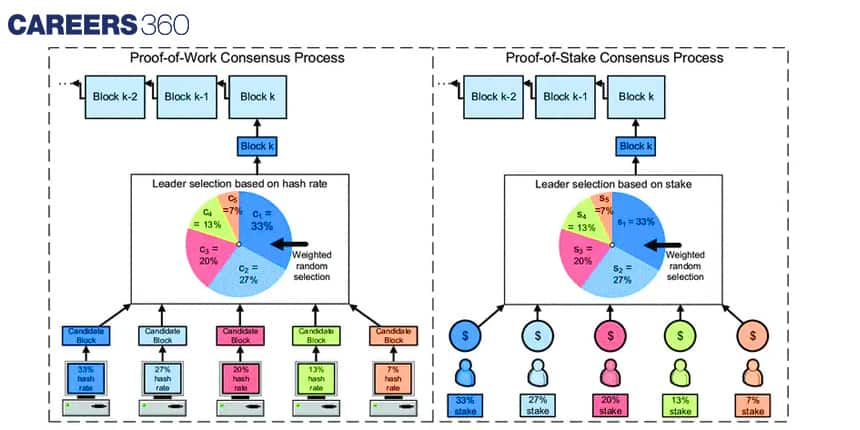
Proof of Work (PoW): Proof of Work is the most well-known consensus algorithm, used by Bitcoin and several other cryptocurrencies. In PoW, nodes (known as "miners") compete to solve complex mathematical problems to validate transactions and create new blocks. The first miner to solve the problem is rewarded with newly minted cryptocurrency. PoW is secure but requires significant computational resources, which makes it slow and energy-intensive.
Proof of Stake (PoS): Proof of Stake is an alternative consensus algorithm that does not require miners to compete in solving mathematical problems. Instead, validators are selected based on the amount of cryptocurrency they "stake" or hold on the network. Validators then take turns validating transactions and creating new blocks. PoS is less energy-intensive than PoW, but it requires a significant amount of cryptocurrency to participate.
Blockchain Type
Public Blockchain: Public Blockchain is an open and decentralised network that anyone can join and participate in. Bitcoin, Ethereum, and Litecoin are examples of public Blockchains. In a public Blockchain, no one controls the network, and transactions are validated through consensus mechanisms such as Proof of Work (PoW) or Proof of Stake (PoS).
Private Blockchain: A private Blockchain is a permissioned network that is restricted to a group of authorised participants. These participants can view and validate transactions, and a designated authority controls who can create new blocks. Private Blockchains are often used by businesses or organisations for internal purposes such as supply chain management or record-keeping.
Hybrid Blockchain: Hybrid Blockchains combine features of both public and private Blockchains. This type of Blockchain is often used by businesses or organisations that want to keep some information private while also maintaining transparency and accountability.
Also Read | Exploring The Cosmos: How Mathematics Powers Space Travel
Cryptography-Related Technologies
Hash Function
A hash function is a mathematical function that takes an input (also known as a message or data) and produces a fixed-size output called a hash. Hash functions are used extensively in Blockchain technology to ensure the security and integrity of the data stored on the Blockchain.
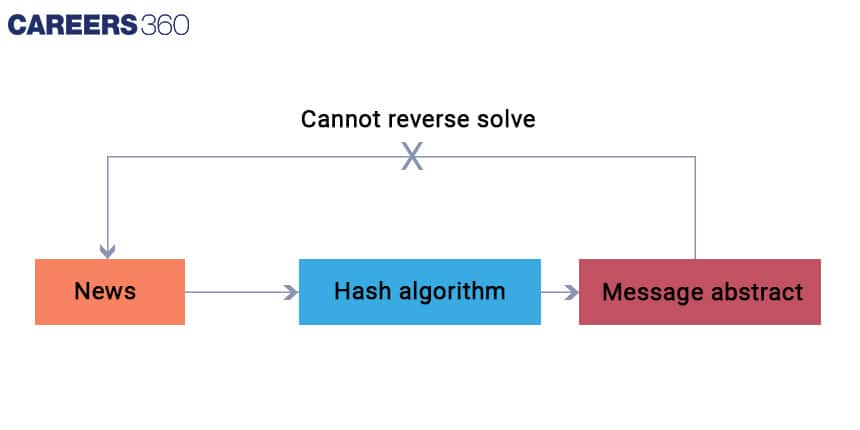
A simple example of a hash function is the "modulo" operator, denoted by the % symbol. Suppose we want to hash a number x and map it to a value in the range [0, 9]. We can define a hash function as follows:
h(x) = x % 10
This function takes the input x and returns the remainder when x is divided by 10. For example, if x = 27, then h(x) = 7, because 27 divided by 10 leaves a remainder of 7.
In practice, more complex hash functions are used that are designed to minimise the probability of collisions.
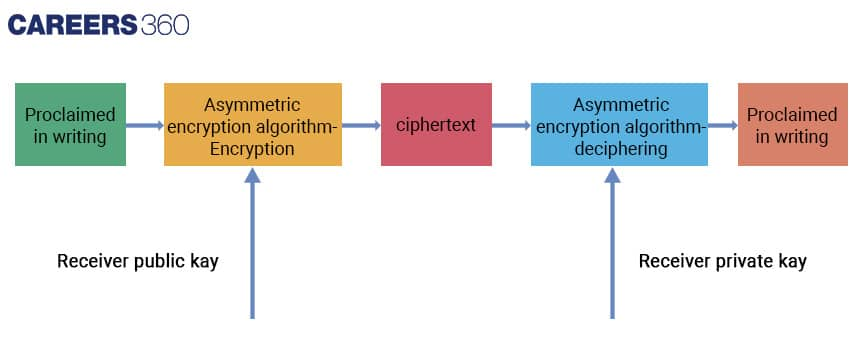
Asymmetric Encryption
Asymmetric encryption, also known as public-key cryptography, is a cryptographic method that uses two different keys to encrypt and decrypt data. Each user has a public key that can be shared with anyone and a private key that must be kept secret.
Potential Applications Of Blockchain
Blockchain technology has the potential to revolutionise many industries and applications. Here are some potential applications of blockchain:
Cryptocurrencies: Blockchain is best known for its use in creating cryptocurrencies like Bitcoin, Ethereum, and others. Cryptocurrencies use blockchain to securely record and verify transactions without the need for a central authority.
Supply chain management: Blockchain can be used to create an immutable record of a product's journey through the supply chain. This can help improve transparency, reduce fraud, and increase efficiency.
Smart contracts: Blockchain can be used to create self-executing smart contracts that automatically enforce the terms of an agreement. This can help reduce the need for intermediaries and increase efficiency.
Voting systems: Blockchain can be used to create secure and transparent voting systems that prevent fraud and increase trust in the electoral process.
Advantages Of Using Blockchain:
Security: Blockchain uses cryptographic algorithms to secure data, making it resistant to unauthorised changes or tampering. Once data is recorded on the blockchain, it becomes almost impossible to modify, making it an extremely secure system.
Decentralisation: Blockchain is a decentralised system, meaning it does not rely on a central authority or intermediary to manage transactions. This makes it more resilient to attacks and more difficult to hack.
Transparency: Blockchain provides a transparent and auditable record of all transactions, which can help reduce fraud and increase accountability.
Challenges Of Using Blockchain:
Scalability: Blockchain technology is still relatively new and is not yet capable of processing large volumes of transactions at high speed. This can be a challenge for applications that require high throughput.
Complexity: Blockchain technology can be complex and difficult to understand, making it challenging for businesses to integrate it into their existing systems.
Energy consumption: The process of mining and verifying transactions on the blockchain requires significant computational power, which can lead to high energy consumption and environmental concerns.
Applications for Admissions are open.
As per latest syllabus. Physics formulas, equations, & laws of class 11 & 12th chapters
JEE Main Important Chemistry formulas
Get nowAs per latest syllabus. Chemistry formulas, equations, & laws of class 11 & 12th chapters
JEE Main high scoring chapters and topics
Get nowAs per latest 2024 syllabus. Study 40% syllabus and score upto 100% marks in JEE
JEE Main Important Mathematics Formulas
Get nowAs per latest syllabus. Maths formulas, equations, & theorems of class 11 & 12th chapters
